## 创建防火墙 ##
1. 安全组是一种虚拟防火墙,具备状态检测和数据包过滤能力,用于在云端划分安全域。通过配置安全组规则,您可以控制安全组内ECS实例的入流量和出流量。
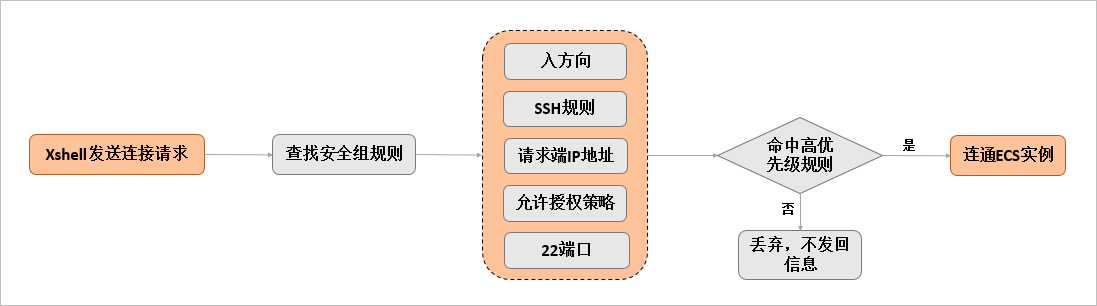
2. 您使用Xshell客户端远程连接Linux系统ECS实例时,当安全组检测到从公网或内网有SSH请求,会逐一检查入方向上安全组规则、发送请求的设备的IP地址是否已存在、优先级是为同类规则第一、授权策略是否为允许、22端口是否开启等。只有匹配到一条安全组规则允许放行该请求时,方才建立数据通信。下图为使用Xshell远程连接Linux系统ECS实例的规则匹配举例。
3. 代码
```
resource "alicloud_security_group" "group" {
name = "sc"
description = "course security group"
vpc_id = alicloud_vpc.vpc.id
}
resource "alicloud_security_group_rule" "allow_22" {
# The type of rule being created.
#Valid options are ingress (inbound) or egress (outbound).
type = "ingress"
# the protocol. Can be tcp, udp, icmp, gre or all.
ip_protocol = "tcp"
#Network type, can be either internet or intranet,
#the default value is internet.
nic_type = "intranet"
# Authorization policy, can be either accept or drop,
#the default value is accept
policy = "accept"
# the range of port numbers relevant to the IP protocol. Default to "-1/-1". When the protocol is tcp or udp, each side port number range from 1 to 65535 and '-1/-1' will be invalid. For example, 1/200 means that the range of the port numbers is 1-200. Other protocols' 'port_range' can only be "-1/-1", and other values will be invalid
port_range = "22/22"
# The target security group ID within the same region.
security_group_id = alicloud_security_group.group.id
# The target IP address range. The default value is 0.0.0.0/0 (which means no restriction will be applied). Other supported formats include 10.159.6.18/12. Only IPv4 is supported
cidr_ip = "0.0.0.0/0"
}
```
## 网络acl ##
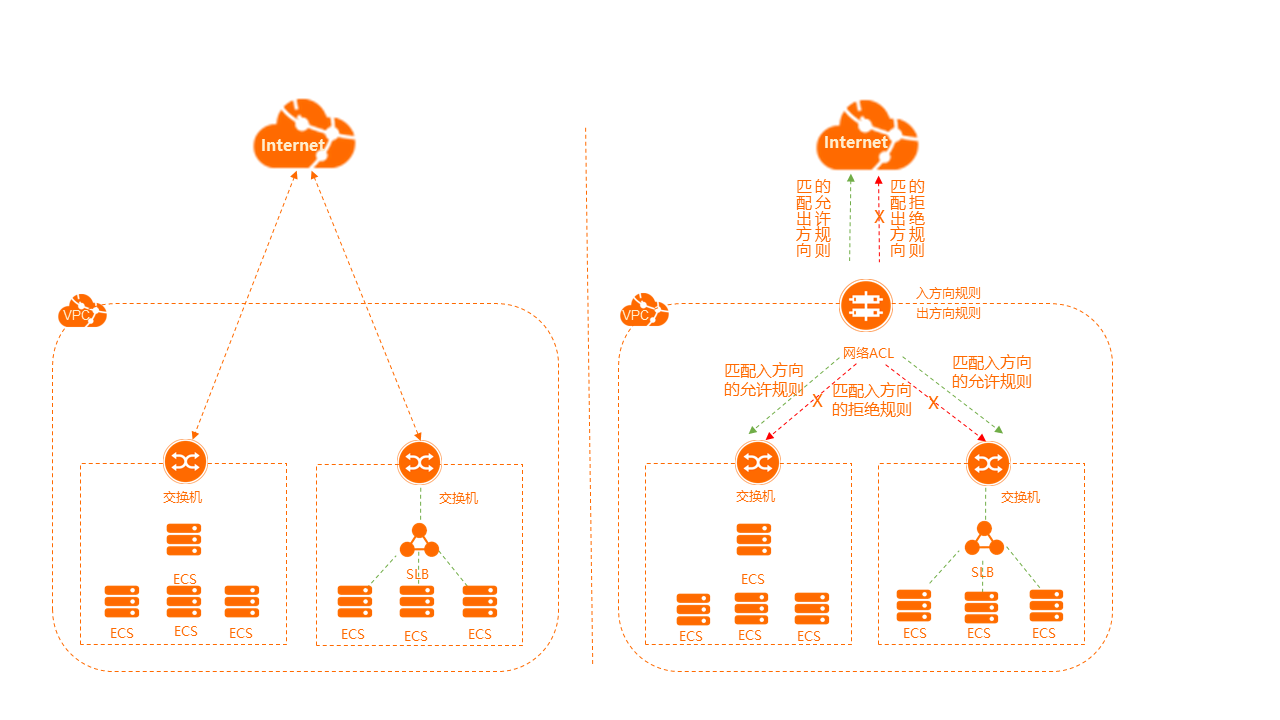
1. 网络访问控制列表(ACL)是 VPC 中的网络访问控制功能,可以将网络 ACL 与交换机进行关联,实现对一个或多个子网流量的访问控制。规则与安全组相似,用户可以对网络 ACL 的规则进行自主设置自定规则。网络 ACL 的规则是无状态的,设置入站规则允许某些请求后,需要同时设置相应的出站规则,否则可能会导致某些请求无法响应。
```
data "alicloud_zones" "default" {
available_resource_creation = "VSwitch"
}
resource "alicloud_vpc" "default" {
cidr_block = "172.16.0.0/12"
vpc_name = "VpcConfig"
}
resource "alicloud_vswitch" "default" {
vpc_id = alicloud_vpc.default.id
vswitch_name = "vswitch"
cidr_block = cidrsubnet(alicloud_vpc.default.cidr_block, 4, 4)
zone_id = data.alicloud_zones.default.ids.0
}
resource "alicloud_network_acl" "default" {
vpc_id = alicloud_vpc.default.id
network_acl_name = "network_acl"
description = "network_acl"
ingress_acl_entries {
description = "tf-testacc"
network_acl_entry_name = "tcp23"
source_cidr_ip = "196.168.2.0/21"
policy = "accept"
port = "22/80"
protocol = "tcp"
}
egress_acl_entries {
description = "tf-testacc"
network_acl_entry_name = "tcp23"
destination_cidr_ip = "0.0.0.0/0"
policy = "accept"
port = "-1/-1"
protocol = "all"
}
resources {
resource_id = alicloud_vswitch.default.id
resource_type = "VSwitch"
}
}
```
- 【概要简介】1.001-简介-本课程体系简介
- 【概要简介】1.002-简介-云的发展趋势
- 【概要简介】1.003-简介-国内主流的云服务平台
- 【概要简介】1.004-简介-Terraform云平台devops的瑞士军刀
- 【快速入门】2.000-快速入门-云后台创建主机
- 【快速入门】2.001-快速入门-创建主机-先查询资源
- 【快速入门】2.002-快速入门-创建主机-阿里云
- 【快速入门】2.003-快速入门-创建主机-亚马逊aws
- 【快速入门】2.100-快速入门-官方网站学习资料
- 【快速入门】2.101-快速入门-Terraform主要的文件.
- 【快速入门】2.102-快速入门-创建虚拟网络
- 【快速入门】1.103-快速入门-创建安全和规则
- 【快速入门】2.104-快速入门-创建云盘
- 【快速入门】2.105-快速入门-创建Ecs主机服务
- 【快速入门】2.200-快速入门-搭建Nginx
- 【快速入门】2.201-快速入门-搭建Nginx-分拆main文件
- 【快速入门】2.203-快速入门-购买固定IP并绑定到主机
- 【快速入门】2.204-快速入门-绑定域名到自己的主页
- 【快速入门】2.205-快速入门-申请免费的https证书并绑定TODO
- 【快速入门】2.300-快速入门-创建Oss存储并搭建静态网站
- 【快速入门】2.300-快速入门-Cdn-TODO
- 【中级进阶】3.101-中级进阶-用Packer创建Wordpress的主机镜像
- 【中级进阶】3.102-中级进阶-利用自己的镜像创建Ecs主机
- 【中级进阶】3.104-中级进阶-用自己镜像搭建负载均衡的Wordpress网站
- 【中级进阶】3.105-中级进阶-利用弹性伸缩ESS创建SLB对应的动态数量的ECS服务器
- 【中级进阶】3.106-中级进阶-自定义Module搭建多个负载均衡的Wordpress网站
- 【中级进阶】3.200-中级进阶-备份多个Wordpress服务器的日志到ossTODO
- 【中级进阶】3.300-中级进阶-创建Ecs快照服务
- 【中级进阶】3.400-中级进阶-Datasource查询
- 【中级进阶】3.500-中级进阶-保存Terraform的state文件
- 【中级进阶】3.600-中级进阶-Variables and environment variables
- 【中级进阶】3.700-中级进阶-Terraform命令解析
- 【高级深入】4.000-高级深入-创建容器镜像服务
- 【高级深入】4.001-高级深入-编译自己的docker镜像并上传到Aliyun cr
- 【高级深入】4.002-高级深入-Terraform创建Kubernetes集群
- 【高级深入】4.003-高级深入-Terraform在Kubernetes集群中部署Wordpress应用
- 【高级深入】4.100-高级深入-使用云服务平台提供的module来创建服务资源
- 【高级深入】4.200-高级深入-同步Terraform的状态.到terraform cloud
- 【高级深入】4.300-高级深入-Terraform的语法
- 【高级深入】4.400-高级深入-Terraform与其Ansible一起使用
- 【高级深入】4.500-高级深入-Terraform的provisioner
- 【高级深入】4.600-高级深入-Snat
- 【高级深入】4.601-高级深入-Dnat
- 4.602-高级深入-Vpc-vpc通信
- 【高级深入】4.603-高级深入-Switch与switch-通信