## 准备签发证书环境
这个在运维主机HDSS-79.host.com上:
#### 1、安装CFSSL
```
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -O /usr/bin/cfssl
wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -O /usr/bin/cfssl-json
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -O /usr/bin/cfssl-certinfo
chmod +x /usr/bin/cfssl*
```
创建证书存放位置(可自己设置):
```
mkdir /opt/certs
cd /opt/certs
```
#### 2、创建生成CA证书签名请求(csr)的JSON配置文件
```
cat /opt/certs/ca-csr.json
{
"CN": "OldboyEdu",
"hosts": [
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
],
"ca": {
"expiry": "175200h"
}
}
```
#### 3、在/opt/certs生成CA证书和私钥
```
cfssl gencert -initca ca-csr.json | cfssl-json -bare ca
```
## 安装etcd
安装机器HDSS7-12,HDSS7-21,HDSS7-22
#### 创建基于根证书的config配置文件
```
cat ca-config.json
{
"signing": {
"default": {
"expiry": "175200h"
},
"profiles": {
"server": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth"
]
},
"client": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
},
"peer": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
```
#### 创建生成自签证书签名请求(csr)的JION配置文件
```
vi etcd-peer-csr.json
{
"CN": "k8s-etcd",
"hosts": [
"10.4.7.11",
"10.4.7.12",
"10.4.7.21",
"10.4.7.22"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
]
}
```
#### 生成etcd证书和私钥
```
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer etcd-peer-csr.json |cfssl-json -bare etcd-peer
```
etcd下载地址:https://github.com/etcd-io/etcd/tags
#### 解压文件
```
wget https://github.com/etcd-io/etcd/releases/download/v3.2.28/etcd-v3.2.28-linux-amd64.tar.gz
tar -zxf etcd-v3.2.28-linux-amd64.tar.gz -C ../
ln -s /opt/etcd-v3.2.28-linux-amd64/ /opt/etcd
mkdir -p /opt/etcd/certs /data/etcd /data/logs/etcd-server
```
#### 创建用户
```
useradd -s /sbin/nologin -M etcd
id etcd
```
#### 证书发生到etcd机器
```
scp ca.pem etcd-peer.pem etcd-peer-key.pem hdss7-12:/opt/etcd/certs
```
#### 启动文件配置
```
#!/bin/sh
./etcd --name etcd-server-7-12 \
--data-dir /data/etcd/etcd-server \
--listen-peer-urls https://10.4.7.12:2380 \
--listen-client-urls https://10.4.7.12:2379,http://127.0.0.1:2379 \
--quota-backend-bytes 8000000000 \
--initial-advertise-peer-urls https://10.4.7.12:2380 \
--advertise-client-urls https://10.4.7.12:2379,http://127.0.0.1:2379 \
--initial-cluster etcd-server-7-12=https://10.4.7.12:2380,etcd-server-7-21=https://10.4.7.21:2380,etcd-server-7-22=https://10.4.7.22:2380 \
--ca-file ./certs/ca.pem \
--cert-file ./certs/etcd-peer.pem \
--key-file ./certs/etcd-peer-key.pem \
--client-cert-auth \
--trusted-ca-file ./certs/ca.pem \
--peer-ca-file ./certs/ca.pem \
--peer-cert-file ./certs/etcd-peer.pem \
--peer-key-file ./certs/etcd-peer-key.pem \
--peer-client-cert-auth \
--peer-trusted-ca-file ./certs/ca.pem \
--log-output stdout
```
#### 执行文件给权限
```
chmod +x /opt/etcd/etcd-server-startup.sh
```
#### 目录授权(这个地方要住权限一定要给)
```
chown -R etcd.etcd /opt/etcd/certs /data/etcd /data/logs/etcd-server
```
#### Supervisor安装部署
```
yum install -y epel-release
yum install -y supervisor
systemctl enable supervisord # 开机自启动
systemctl start supervisord # 启动supervisord服务
```
#### Supervisor配置etcd启动文件
```
vi /etc/supervisord.d/etcd-server.ini
[program:etcd-server]
command=/opt/etcd/etcd-server-startup.sh ; the program (relative uses PATH, can take args)
numprocs=1 ; number of processes copies to start (def 1)
directory=/opt/etcd ; directory to cwd to before exec (def no cwd)
autostart=true ; start at supervisord start (default: true)
autorestart=true ; retstart at unexpected quit (default: true)
startsecs=30 ; number of secs prog must stay running (def. 1)
startretries=3 ; max # of serial start failures (default 3)
exitcodes=0,2 ; 'expected' exit codes for process (default 0,2)
stopsignal=QUIT ; signal used to kill process (default TERM)
stopwaitsecs=10 ; max num secs to wait b4 SIGKILL (default 10)
user=etcd ; setuid to this UNIX account to run the program
redirect_stderr=true ; redirect proc stderr to stdout (default false)
stdout_logfile=/data/logs/etcd-server/etcd.stdout.log ; stdout log path, NONE for none; default AUTO
stdout_logfile_maxbytes=64MB ; max # logfile bytes b4 rotation (default 50MB)
stdout_logfile_backups=4 ; # of stdout logfile backups (default 10)
stdout_capture_maxbytes=1MB ; number of bytes in 'capturemode' (default 0)
stdout_events_enabled=false ; emit events on stdout writes (default false)
killasgroup=true
stopasgroup=true
```
#### 更新supervisord
```
supervisorctl update
supervisorctl status
```
#### 验证etcd服务
```
cd /opt/etcd/
./etcdctl cluster-health
./etcdctl member list
```
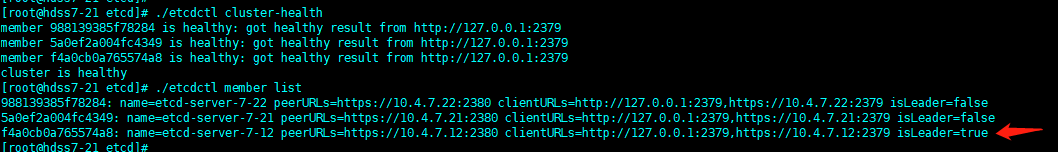
### 到这里etcd已经部署完成了
### 4、里面其实存储了很多的key,如何查看和管理这些key,需要使用一个小工具,叫做etcdkeeper:
### 下载etcd,在etcd节点选一台
```
cd /opt/src
wget https://github.com/evildecay/etcdkeeper/releases/download/v0.7.5/etcdkeeper-v0.7.5-linux_x86_64.zip
解开压缩包,需安装unzip: yum install unzip -y
unzip etcdkeeper-*-linux_x86_64.zip
rm etcdkeeper-*-linux_x86_64.zip
mv etcdkeeper ../
ln -s /opt/etcdkeeper-0.7.5/ /opt/etcdkeeper
cd /opt/etcdkeeper
chmod +x etcdkeeper
```
#### 编写一个服务文件该服务文件主要用于在后台运行etcd程序,用以提供http服务
```
vi /lib/systemd/system/etcdkeeper.service
[Unit]
Description=etcdkeeper service
After=network.target
[Service]
Type=simple
ExecStart=/opt/etcdkeeper/etcdkeeper -h 10.4.7.12 -p 8800
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=on-failure
PrivateTmp=true
[Install]
WantedBy=multi-user.target
```
#### 服务的控制
```
systemctl start etcdkeeper 启动etcdkeeper服务
systemctl stop etcdkeeper 停止etcdkeeper服务
systemctl enable etcdkeeper.service 设置开机自启动
systemctl disable etcdkeeper.service 停止开机自启动
```
#### 测试访问http://10.4.7.12:8800/etcdkeeper
- 空白目录
- k8s
- k8s介绍和架构图
- 硬件环境和准备工作
- bind9-DNS服务部署
- 私有仓库harbor部署
- k8s-etcd部署
- api-server部署
- 配置apiserver L4代理
- controller-manager部署
- kube-scheduler部署
- node节点kubelet 部署
- node节点kube-proxy部署
- cfss-certinfo使用
- k8s网络-Flannel部署
- k8s网络优化
- CoreDNS部署
- k8s服务暴露之ingress
- 常用命令记录
- k8s-部署dashboard服务
- K8S平滑升级
- k8s服务交付
- k8s交付dubbo服务
- 服务架构图
- zookeeper服务部署
- Jenkins服务+共享存储nfs部署
- 安装配置maven和java运行时环境的底包镜像
- 使用blue ocean流水线构建镜像
- K8S生态--交付prometheus监控
- 介绍
- 部署4个exporter
- 部署prometheus server
- 部署grafana
- alert告警部署
- 日志收集ELK
- 制作Tomcat镜像
- 部署ElasticSearch
- 部署kafka和kafka-manager
- filebeat镜像制作
- 部署logstash
- 部署Kibana
- Apollo交付到Kubernetes集群
- Apollo简介
- 交付apollo-configservice
- 交付apollo-adminservice
- 交付apollo-portal
- k8s-CICD
- 集群整体架构
- 集群安装
- harbor仓库和nfs部署
- nginx-ingress-controller服务部署
- gitlab服务部署
- gitlab服务优化
- gitlab-runner部署
- dind服务部署
- CICD自动化服务devops演示
- k8s上服务日志收集
