## 基于文件的服务发现
## 一、概述
定义一组资源”子“配置文件(json格式或者yaml格式),里面只存放需要采集的targets信息,此种方式可以被prometheus动态获取到,而不需要重启。
基于文件的服务发现仅仅略优于静志配置的服务发现方式,它不依赖于任何平台或第三方服务,因而也是最为简单和通用的实现方式。
prometheus server 定期从文件中加载target 信息(prometheus-server pull指标发现机制-job_name 获取要 pu 的对象target)文件它含有定义的target 列表,以及可选的标签信息
### 1.1 原理
它读取一组包含零个或多个<static_config>列表的文件,对所有定义的文件的变更通过磁盘监视被检测到并立即应用,文件可以以YAML或JSON 格式提供。文件必须包含一个静态配置的列表
文件内容也会在指定的刷新间隔时间内定期重新读取。(在去读取files的时候,可以去配置Refresh interval,如果没有配置,这里有个默认值是5m钟的,另外一个就是在配置文件自动发现的时候,支持通配符这样一个模式。)
### 1.2 实验描述
* 定义一个服务发现的目标文件targets.yml
<br><hr><br>
## 二、定义一个服务发现的目标文件targets.yml
### 2.1 创建targets.yaml文件
接下来我们来创建一个用于服务发现的目标文件,在与 prometheus.ym文件目录下面创建个名为 targets/targets.yml的文件,内容
cd /data/docker-prometheus/prometheus
mkdir targets -p
vi targets/tragets.yml
把简单的不需要额外参数的都放进去这个配置文件,如下图所示
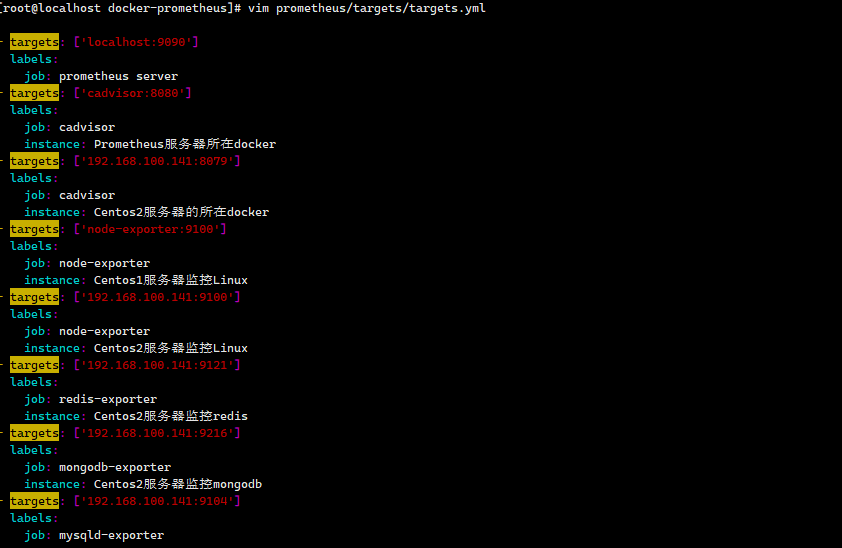
- targets: ['localhost:9090']
labels:
job: prometheus server
instance:prometheus Server
- targets: ['cadvisor:8080']
labels:
job: cadvisor
instance: Prometheus服务器所在docker
- targets: ['192.168.100.141:8079']
labels:
job: cadvisor
instance: Centos2服务器的所在docker
- targets: ['node-exporter:9100']
labels:
job: node-exporter
instance: Centos1服务器监控Linux
- targets: ['192.168.100.141:9100']
labels:
job: node-exporter
instance: Centos2服务器监控Linux
- targets: ['192.168.100.141:9121']
labels:
job: redis-exporter
instance: Centos2服务器监控redis
- targets: ['192.168.100.141:9216']
labels:
job: mongodb-exporter
instance: Centos2服务器监控mongodb
- targets: ['192.168.100.141:9104']
labels:
job: mysqld-exporter
instance: Centos2服务器监控mysql
- targets: ['192.168.100.141:9113']
labels:
job: nginx-exporter
instance: Centos2服务器监控nginx
- targets: ['192.168.100.141:9419']
labels:
job: rabbitmq-exporter
instance: Centos2服务器监控rabbitmq
- targets: ['192.168.100.141:9256']
labels:
job: process-exporter
instance: Centos2服务器监控进程
- targets: ['192.168.100.58:8182']
labels:
job: golang-exporter
instance: Centos3服务器监控go自定义程序
再修改prometheus配置
vim prometheus/prometheus.yml
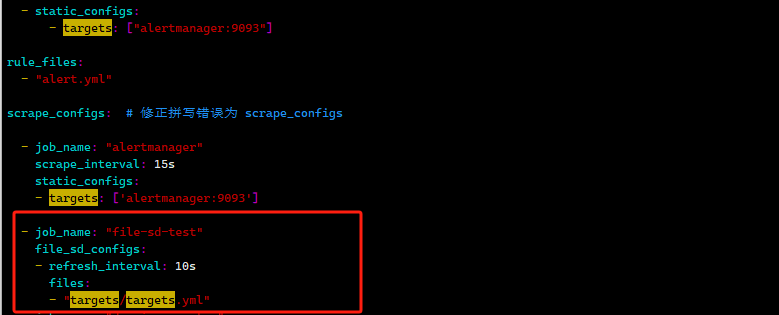
- job_name: "file-sd-test"
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/targets.yml"
保存后输入命令更新:
curl -XPOST http://localhost:9090/-/reload
成功监听
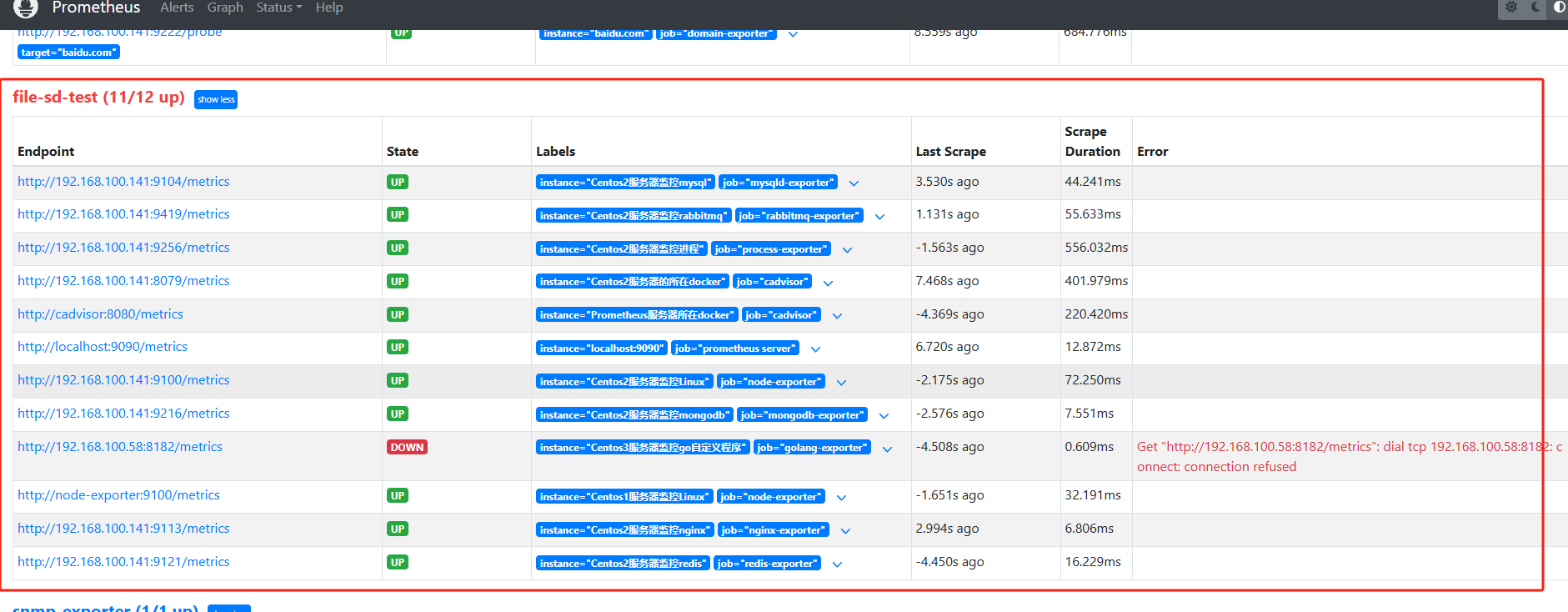
其他监控配置
#domain
vim prometheus/targets/domain.yml
- targets:
- 'qq.com'
- 'baidu.com'
#snmp
vim prometheus/targets/snmp.yml
- targets:
- 192.168.100.141
#blockerbox_http
vim prometheus/targets/blockerbox_http.yml
- targets:
- https://www.baidu.com
- https://wy.ldw520.top
#blockerbox_tcp
vim prometheus/targets/blockerbox_tcp.yml
- targets:
- 192.168.28.87:9090
- 192.168.100.141:9100
#blockerbox_icmp
vim prometheus/targets/blockerbox_icmp.yml
- targets:
- 192.168.100.87
- 192.168.100.141
再修改prometheus配置
vim prometheus/prometheus.yml
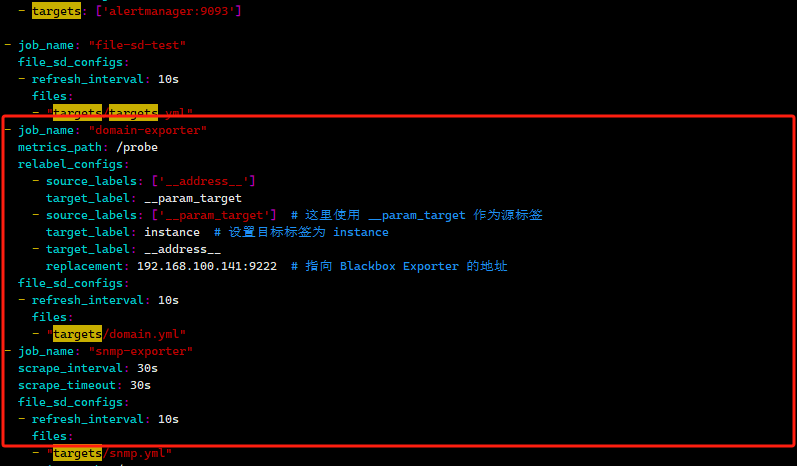
- job_name: "domain-exporter"
metrics_path: /probe
relabel_configs:
- source_labels: ['__address__']
target_label: __param_target
- source_labels: ['__param_target'] # 这里使用 __param_target 作为源标签
target_label: instance # 设置目标标签为 instance
- target_label: __address__
replacement: 192.168.100.141:9222 # 指向 Blackbox Exporter 的地址
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/domain.yml"
- job_name: "snmp-exporter"
scrape_interval: 30s
scrape_timeout: 30s
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/snmp.yml"
metrics_path: /snmp
params:
module: [if_mib]
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: 192.168.100.141:9116
- job_name: "blackbox_http"
metrics_path: /probe
params:
module: [http_2xx]
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/blackbox_http.yml"
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: blackbox_exporter:9115
- job_name: "blackbox_tcp"
metrics_path: /probe
params:
module: [tcp_connect]
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/blackbox_tcp.yml"
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: blackbox_exporter:9115
- job_name: "blackbox_icmp"
metrics_path: /probe
params:
module: [icmp]
file_sd_configs:
- refresh_interval: 10s
files:
- "targets/blackbox_icmp.yml"
relabel_configs:
- source_labels: [__address__]
target_label: __param_target
- source_labels: [__param_target]
target_label: instance
- target_label: __address__
replacement: blackbox_exporter:9115
保存后输入命令更新:
curl -XPOST http://localhost:9090/-/reload
成功监听
- Prometheus教程
- 一. dokcer 安装
- 二. 安装docker-compose
- 三. docker-compose安装Prometheus
- 四. 配置grafana的数据源
- 五. Prometheus的Exporter
- 六. Prometheus的基本术语
- 七. 监控Linux
- 八. 监控redis和mongodb
- 九. 监控mysql数据库
- 十. 监控go程序
- 十一. 监控nginx
- 十二. 监控消息队列
- 十三. 监控docker
- 十四. 监控进程
- 十五. 域名监控
- 十六. SNMP监控
- 十七. 黑盒监控
- 十八. 自定义监控
- 十九. go实现自定义监控
- 二十. 服务发现概述
- 二十一. 基于文件的服务发现
- 二十二. 基于Consul的服务发现
- 二十三. relabeling机制
