[TOC]
# 二进制安装
## 下载traefik包
```shell
curl -L -o /usr/local/src/traefik_v2.10.4_linux_amd64.tar.gz https://github.com/traefik/traefik/releases/download/v2.10.4/traefik_v2.10.4_linux_amd64.tar.gz
```
## 解压traefik
```shell
mkdir -p /app/traefik/{config/{dynamic,k8s-crd-rbac},pki,logs}
tar xvf /usr/local/src/traefik_v2.10.4_linux_amd64.tar.gz -C /app/traefik/
```
## 可选:k8s创建crd及rbac资源
>[info] 说明: `traefik` 自动发现(providers) `kubernetesIngress` 和 `Kubernetes IngressRoute(kubernetesCRD)` 有配置才需要执行以下步骤
```bash
cd /app/traefik/config/k8s-crd-rbac
curl -O https://raw.githubusercontent.com/traefik/traefik/v2.10/docs/content/reference/dynamic-configuration/kubernetes-crd-definition-v1.yml
curl -O https://raw.githubusercontent.com/traefik/traefik/v2.10/docs/content/reference/dynamic-configuration/kubernetes-crd-rbac.yml
kubectl apply -f ./kubernetes-crd-definition-v1.yml
kubectl apply -f ./kubernetes-crd-rbac.yml
kubectl create sa traefik-ingress-controller
kubectl describe secret `kubectl describe sa traefik-ingress-controller | awk '/Tokens/ {print $2}'`
```
## traefik 配置文件
```yaml
# 全局配置
global:
checkNewVersion: true
sendAnonymousUsage: true
# Entrypoints 配置
# web,webSecurity 是Entrypoints名称,可以自定义名称。推荐使用 web,webSecurity
# 注意:traefik, metrics 是内建Entrypoints名称。
entryPoints:
web:
address: ":80"
webSecurity:
address: ":443"
traefik:
address: ":9000"
metrics:
address: ":9100"
# traefik日志设置
# https://doc.traefik.io/traefik/observability/logs/
log:
filePath: "/app/traefik/logs/traefik.log"
format: json
level: DEBUG
# 业务访问日志设置
# https://doc.traefik.io/traefik/observability/access-logs/
accessLog:
filePath: "/app/traefik/logs/access.log"
# 异步写入日志,Traefik 在将日志行写入所选输出之前将保留在内存中的数量
bufferingSize: 100
format: json
fields:
defaultMode: keep
names:
StartUTC: drop
# ClientAddr: drop
# traefik动态发现的提供商
# https://doc.traefik.io/traefik/providers/overview/
providers:
file:
directory: "/app/traefik/config/dynamic"
watch: true
kubernetesIngress:
endpoint: "https://192.168.32.182:6443"
certAuthFilePath: "/app/traefik/pki/ca.crt" # 使用 kubernetes 根证书
token: "" # 上面创建的sa对应的token值
kubernetesCRD:
endpoint: "https://192.168.32.182:6443"
certAuthFilePath: "/app/traefik/pki/ca.crt" # 使用 kubernetes 根证书
token: "" # 上面创建的sa对应的token值
api:
# 启动dashboard页面
dashboard: true
# 非安全访问 dashboard 页面,生产环境不建议开启
# insecure: true
# 健康检查
ping: true
# traefik metrics数据
metrics:
prometheus:
entryPoint: metrics
```
## 创建 systemd 服务文件
```shell
cat <<'EOF' | sudo tee /usr/lib/systemd/system/traefik.service >> /dev/null
[Unit]
Description=traefik Server
Documentation=https://doc.traefik.io/traefik/
Wants=network.service
After=network.service
[Service]
Type=simple
ExecStart=/app/traefik/traefik --configfile /app/traefik/config/traefik.yml
Restart=on-failure
[Install]
WantedBy=multi-user.target
EOF
```
## 启动traefik服务
```shell
systemctl daemon-reload
systemctl start traefik.service
```
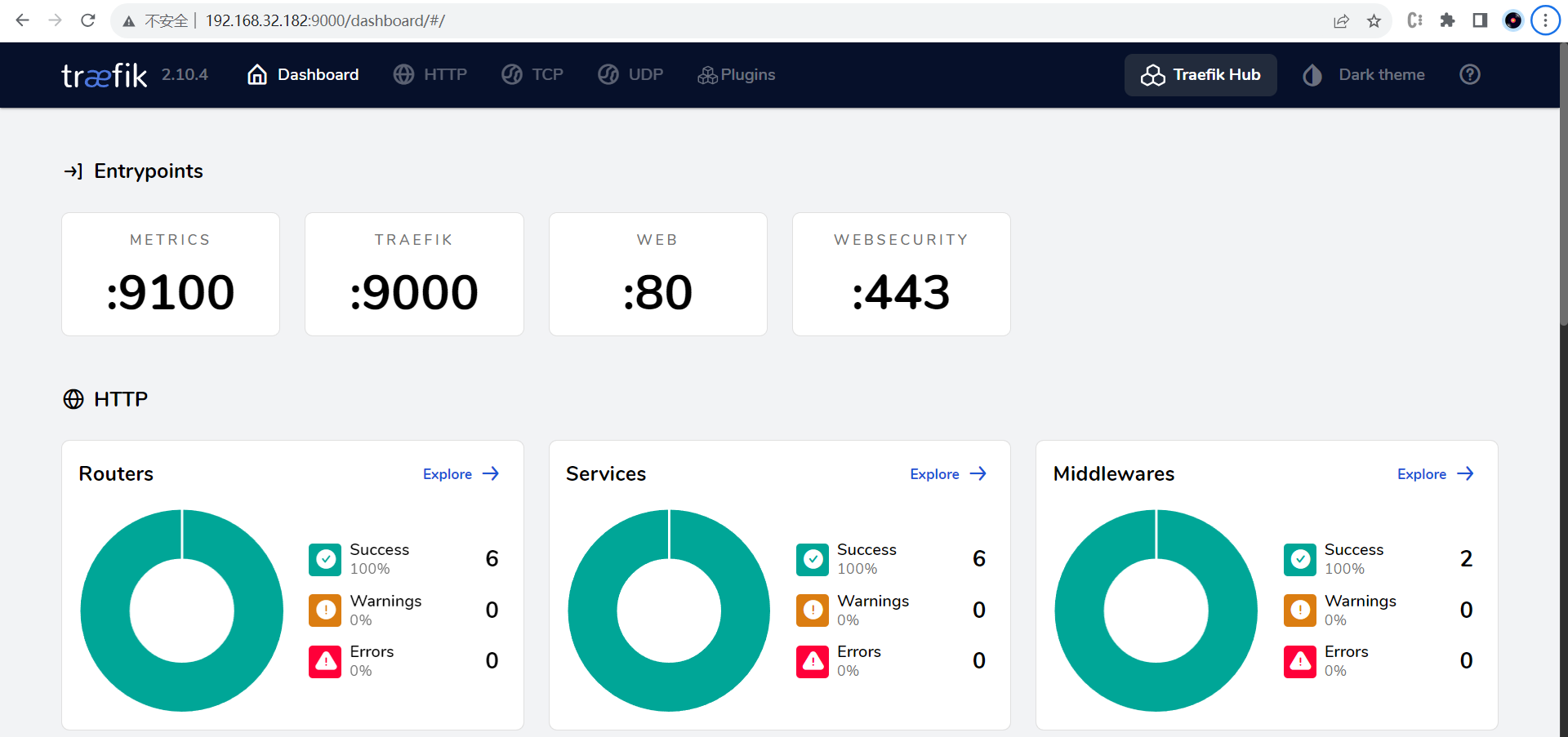
## 访问 dashboard 页面
### 非安全访问
1. 在 traefik 配置文件中,`api` 字段下添加一对 `insecure: true` 的配置。
2. 重启 traefik 服务。
3. 使用 http://{traefik ip}:{traefik port} 访问,{traefik port} 默认是 `8080` 端口
### 安全访问
1. 在 k8s 集群添加 `IngressRoute` 资源
```yaml
cat <<- 'EOF' | kubectl apply -f -
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: dashboard
spec:
entryPoints:
- web
routes:
- match: PathPrefix(`/dashboard`) || PathPrefix(`/api`)
kind: Rule
services:
- name: api@internal
kind: TraefikService
EOF
```
2. 访问 `http://{traefik web}:{traefik web port}/dashboard/` 地址
>[danger] 注意:path路径必须是 `/dashboard/` , 否则抛出 `404 page not found` 异常
# helm 安装
- 前言
- 架构
- 部署
- kubeadm部署
- kubeadm扩容节点
- 二进制安装基础组件
- 添加master节点
- 添加工作节点
- 选装插件安装
- Kubernetes使用
- k8s与dockerfile启动参数
- hostPort与hostNetwork异同
- 应用上下线最佳实践
- 进入容器命名空间
- 主机与pod之间拷贝
- events排序问题
- k8s会话保持
- 容器root特权
- CNI插件
- calico
- calicoctl安装
- calico网络通信
- calico更改pod地址范围
- 新增节点网卡名不一致
- 修改calico模式
- calico数据存储迁移
- 启用 kubectl 来管理 Calico
- calico卸载
- cilium
- cilium架构
- cilium/hubble安装
- cilium网络路由
- IP地址管理(IPAM)
- Cilium替换KubeProxy
- NodePort运行DSR模式
- IP地址伪装
- ingress使用
- nginx-ingress
- ingress安装
- ingress高可用
- helm方式安装
- 基本使用
- Rewrite配置
- tls安全路由
- ingress发布管理
- 代理k8s集群外的web应用
- ingress自定义日志
- ingress记录真实IP地址
- 自定义参数
- traefik-ingress
- traefik名词概念
- traefik安装
- traefik初次使用
- traefik路由(IngressRoute)
- traefik中间件(middlewares)
- traefik记录真实IP地址
- cert-manager
- 安装教程
- 颁布者CA
- 创建证书
- 外部存储
- 对接NFS
- 对接ceph-rbd
- 对接cephfs
- 监控平台
- Prometheus
- Prometheus安装
- grafana安装
- Prometheus配置文件
- node_exporter安装
- kube-state-metrics安装
- Prometheus黑盒监控
- Prometheus告警
- grafana仪表盘设置
- 常用监控配置文件
- thanos
- Prometheus
- Sidecar组件
- Store Gateway组件
- Querier组件
- Compactor组件
- Prometheus监控项
- grafana
- Querier对接grafana
- alertmanager
- Prometheus对接alertmanager
- 日志中心
- filebeat安装
- kafka安装
- logstash安装
- elasticsearch安装
- elasticsearch索引生命周期管理
- kibana安装
- event事件收集
- 资源预留
- 节点资源预留
- imagefs与nodefs验证
- 资源预留 vs 驱逐 vs OOM
- scheduler调度原理
- Helm
- Helm安装
- Helm基本使用
- 安全
- apiserver审计日志
- RBAC鉴权
- namespace资源限制
- 加密Secret数据
- 服务网格
- 备份恢复
- Velero安装
- 备份与恢复
- 常用维护操作
- container runtime
- 拉取私有仓库镜像配置
- 拉取公网镜像加速配置
- runtime网络代理
- overlay2目录占用过大
- 更改Docker的数据目录
- Harbor
- 重置Harbor密码
- 问题处理
- 关闭或开启Harbor的认证
- 固定harbor的IP地址范围
- ETCD
- ETCD扩缩容
- ETCD常用命令
- ETCD数据空间压缩清理
- ingress
- ingress-nginx header配置
- kubernetes
- 验证yaml合法性
- 切换KubeProxy模式
- 容器解析域名
- 删除节点
- 修改镜像仓库
- 修改node名称
- 升级k8s集群
- 切换容器运行时
- apiserver接口
- 其他
- 升级内核
- k8s组件性能分析
- ETCD
- calico
- calico健康检查失败
- Harbor
- harbor同步失败
- Kubernetes
- 资源Terminating状态
- 启动容器报错
